0 Preface
Short Message Service (SMS) is an end-to-end data communication method provided by the GSM network; it can be text, voice or picture information. SMS adopts the store-and-forward mechanism, that is, when a mobile phone user sends an SMS message, the message is not directly received by the receiver, but is received by the short message center of the user's network, and then the short message center is sent to the receiver. Send a notification command to inform the recipient to download the message from the short message center. This mechanism has great convenience and flexibility, making it an important communication method for mobile phone users.
Although the short message was originally designed as a reminder of voice E-mail, it quickly became a very popular form of communication between the individual and the business community. At present, many places have carried out services for banking services through SMS, or sent information related to business. When sending sensitive information such as bank accounts, passwords, and identification numbers, people are most worried that the information may be intercepted or sent to people who swindle such information. The message format adopted by the existing GSM short message communication is open and predictable, the source address is falsified, and is clear in the whole transmission process, so the short message communication is not always reliable. For these sensitive applications, GSM users should be able to choose a secure communication to ensure that the information is not properly read and falsified, so it is necessary to provide an encrypted communication method on the mobile terminal.
At present, there are two main implementations of short message encryption: 1 Based on encrypted communication between the terminal and the server. It requires the server to work together, and the text message is still transmitted in clear text in the core network, and there is still the risk of being intercepted. 2 end-to-end encrypted communication. It needs to be designed on the mobile phone terminal or card, the implementation is relatively small, and the security is higher. This paper presents a scheme based on smart card implementation of encrypted short message communication, which has the characteristics unrelated to the mobile terminal and better practicability.
1 short message communication network structure
GSM short message communication is to transmit data through a signaling channel. According to its sending and receiving short messages, it can be divided into two types: mobile start (MO) and mobile terminated (MT). The process of sending and receiving can be described as follows: The short message sender submits the MO short message to the short message service center ( SMSC), which is responsible for relaying, storing or forwarding short messages between the base station and the SME; the mobile station (MS) to The SMSC protocol can transmit the short message of MO or MT, the SMS gateway receives the short message sent by the SMSC, queries the HLR for routing information, and transmits the short message to the switching center of the base station where the receiver is located, and completes the short message data by the SMSC. Exchange establishment. The GSM network structure for short message communication is given below. The point-to-point short message service defined in the GSM standard enables short messages to be passed between the mobile station and the short message service center. These service centers are connected to the GSM network through a specific Mobile Switching Center (MSC) called SMC-GMSC, as shown in Figure 1.
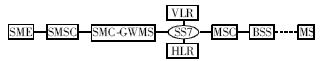
Figure 1 short message communication architecture
The VLR (Visitor Location Register) is a visitor location register, which contains a database of user temporary information. The HLR (Home Location Register) is a home location register, which is used to permanently store a database of management users and service records, which is generated by the SMSC.
Short messages are transmitted over the GSM network, and the network itself does not provide corresponding security mechanisms such as mutual authentication, end-to-end security, non-repudiation, and user anonymity. Therefore, the current short message network does not meet the three basic requirements of secure communication, namely the integrity, confidentiality and validity of information.
2 encryption algorithm and its implementation on smart cards
The above communication security issues can be solved by means of information encryption technology. At present, information encryption is mostly based on a key-based method. This type of method mainly has two systems: symmetric key and non-pair key.
Common symmetric key algorithms are AES, DES, 3DES, and IDEA. A symmetric key is characterized by the same decryption as the encryption key. Such algorithms have the advantages of fast encryption/decryption speed and small space occupied by the operation, but there are disadvantages such as key exchange and complex key management. A typical asymmetric method is RSA, which is based on the principle of integer decomposition and uses a method of analog-to-digital operation. The degree of information confidentiality of the asymmetric method depends on the difficulty of solving the specified mathematical problem. At present, there are exponential decomposition and discrete logarithm problems. The difficulty of the algorithm is directly proportional to the difficulty of the corresponding mathematical problem. Unlike symmetric methods, asymmetric methods use both private and public keys. The public key can be exposed to all users, the sender is encrypted with the public key, and the recipient is decrypted with the private key. This method has high security and convenient key management, and has broad application prospects in commercial systems.
The SIM card is used as a smart card for carrying user identification information in GSM. A smart card is a small device with relatively weak computing power. It usually uses encryption/decryption algorithms such as DES, 3DES, and RSA to improve system security. For the DES and 3DES symmetric key algorithm, it is mainly a simple shift operation, so it can be implemented well with a normal smart card. In the implementation of the RSA algorithm, a large exponential modulo operation that requires a high computational speed is required, and an 8-bit CPU is difficult to perform. Therefore, in some high-security cryptographic microcontroller card chips (such as AT90SC1616C), a coprocessor CAU with dedicated encryption/decryption operations is set. Figure 2 shows a block diagram of a smart card chip with a coprocessor [3]. With the deep research of asymmetric key algorithm and the introduction of 32-bit CPU card, public key algorithms such as ECC can be well implemented on smart cards without coprocessor [4].
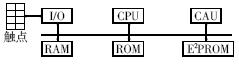
Figure 2 Smart card with coprocessor
Using the achievable encryption algorithms on the smart card, the smart card's input/output data can be encrypted and the corresponding key negotiated. The following will analyze the encryption algorithm on the smart card and select an algorithm suitable for end-to-end SMS encryption.
3 Smart card based short message security mechanism design
End-to-end short message security communication mechanism to solve the data format design of secure short messages, smart card-based key agreement mechanism, message encryption algorithm selection and the design of the entire security process for short message editing, encryption, sending and receiving through smart cards .
3. 1 Secure Short Message Packet Design
Short messages can be divided into uplink and downlink short messages. Its data format mainly includes two parts: protocol data unit parameters and user data. In the protocol data parameter part, the short message type, source address, destination address, protocol flag, encoding mode, and user data header are mainly defined. The TP-PID field can distinguish whether the short message is received by the mobile phone or received by the SIM card, and the TP-MT flag can distinguish the short message from the uplink and the downlink. The maximum usable length of the user data portion is 140 Bytes. Since the parameters of the short message transmission protocol data unit have their fixed format, the space that can be utilized to implement the secure short message is only the payload portion of the user data. In this section, you can define the header and encryption information for the secure short message and an optional numeric summary. The secure short message data header defines information such as security parameters of the encrypted short message, and the application encapsulates the request and interprets the short message according to the data header. The specific data format is shown in Figure 3 [5].
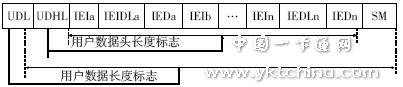
Figure 3 Secure Short Message Data Format
The IEI is an information element flag, which is used to indicate the command header and length and whether there are subsequent messages. Some security-related parameters are defined in the command header, namely the security parameter flag (SPI), the key identifier (KIC), the key identifier (KID) such as the digital digest, and the counter (CNTR) to prevent replay attacks. The secure data part is an encrypted short message. Its specific format is as follows:
![]()
3. 2 Session Key Agreement
3. 2. 1 Guidelines for system design
Due to the characteristics of the smart card device itself, such as low computing power and small storage space, there must be a compromise between security strength, protocol security and efficiency when implementing SMS encryption. There are two points to consider when choosing an encryption algorithm and protocol design:
(1) The computing power and limited memory of smart card devices. Careful selection of public key algorithms and encryption algorithms is necessary.
(2) The payload of the short message. The user available part, typically 140Bytes. Therefore the protocol design must be as efficient as possible. Despite the above limitations, the design cannot be exchanged for efficiency at the expense of safety. The security mechanism must meet the following requirements:
(1) security;
(2) The computational complexity is low;
(3) Ability to implement key exchange;
(4) Easy to implement and use.
Moderation Board,Foldable Flipchart,Art Easel Stand,Digital Flipchart
Dongguan Aoxing Audio Visual Equipment CO.,Ltd , https://www.aoxingaudio.com